The “sticky keys” backdoor method has been a favorite for hackers for years and it’s been gaining popularity as a malware-free persistence method. This backdoor method gives an attacker pre-authentication, SYSTEM-level access to a target remotely over RDP or locally via the console.
The backdoor can be installed in one of two ways:
- Copy cmd.exe over sethc.exe or utilman.exe
- Set cmd.exe as the debugger for sethc.exe or utilman.exe
The sethc.exe backdoor can be triggered by pressing the shift key five times in rapid succession. The utilman.exe backdoor can be triggered by pressing windows+u.
Hunting Backdoors
Checking for these backdoors during a penetration test would be a very labor-intensive task, so why not automate it? I put together a proof-of-concept script called Sticky Keys Hunter.
While developing the script, I thought what better network than the Internet to work out the kinks and timing challenges. Shodan makes simple work of finding targets on the Internet to test. Querying for the default RDP port, port:3389, returns approximately 5.1 million services. I grabbed a list of 10k targets to test out the script.
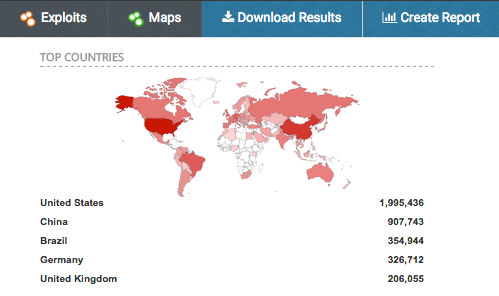
The sticky keys hunter scanning is pretty slow where each host takes between 7-10 seconds on average to execute the script. I have yet to figure out a good way to multithread this process short of using multiple servers or rewriting the tool to work at the protocol level. So right now a single host scanning 10k targets takes about a week. Even with the slow scans, the script’s initial run against a 10k host target list yielded 11 backdoors.
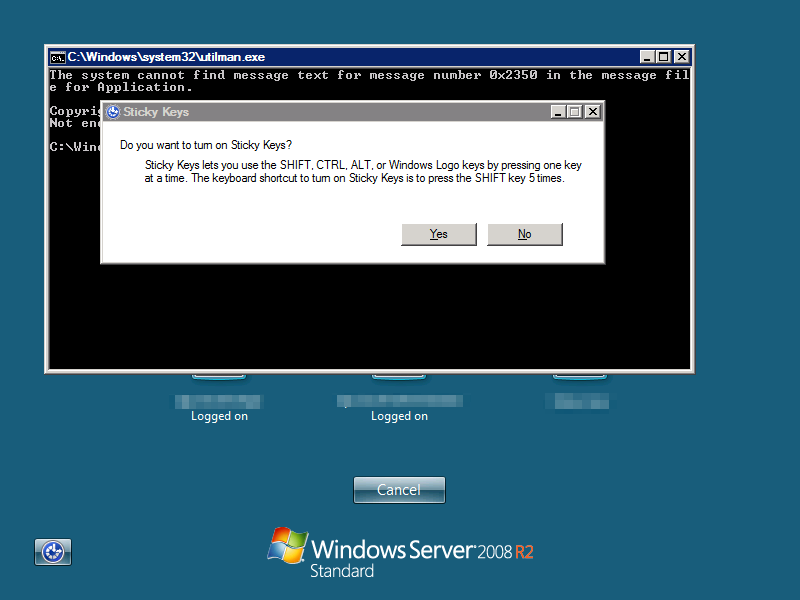
Below is a screenshot of a sticky keys backdoored server in the UK.
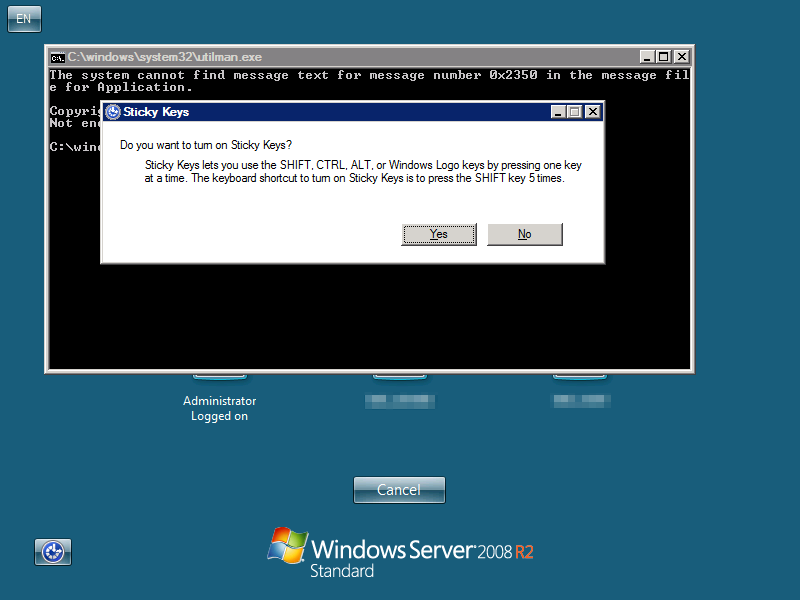
Below is a screenshot of an observed utilman backdoor in Malaysia.
Disclaimer: No systems were exploited during this research. Sticky Keys Hunter should only be for legitimate penetration testing and research purposes.
